Email Spoofing Attack using a PHP Script
If you use emails for daily communication, you must be aware of fake emails. This is known as email spoofing, meaning impersonating someone else while sending an email. Let me show you how attackers spoof emails using a simple PHP script.
Disclaimer
This article is not to encourage viewers to perform spoofing attacks. Instead, it is to help you spot red flags and protect yourself and your organization from fake emails.
Spoofing emails using a PHP script
<?php
$to = "victim@gmail.com";
$subject = "Spoofing email attack";
$message = "Beware of my spoofing attack! I plan to steal your money.";
$headers = "From: spoofer@travelworld.com\r\n";
$headers .= "Reply-To: spoofer@gmail.com\r\n";
$headers .= "X-Mailer: PHP/" . phpversion();
// Send email
if (mail($to, $subject, $message, $headers)) {
echo "Email sent successfully!";
} else {
echo "Failed to send email.";
}
?>
To send a spoofed email, start by creating a PHP file named mail.php. Inside this script, define the recipient’s email address, the subject, and the body of the message.
For this example, I will impersonate as the employer of a fictitious company called TravelWorld. Note that I don’t own the domain travelworld.com so I would like to receive replies from the victim on a different email address. To do this, I will specify a different reply-To address—one that I do have access to. The reason why most spoofing attacks succeed is because people don’t check the reply-To address. Attackers exploit this oversight to trick victims into believing that they are communicating with a genuine employee.
Finally, use PHP’s built-in mail() function, passing it these variables as arguments. The rest of the script simply reports whether the message was sent successfully or not.
Now, save this file and upload it to a server. For this demo, I’m using a low-cost shared hosting service that costs less than one US dollar per month. The affordability and simplicity of shared hosting makes spoofing attacks very convenient and economical.
After the file is uploaded on the server which I can execute through a web browser.
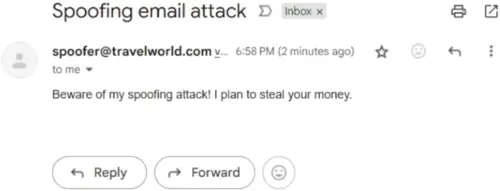
Since I put my own email address as the recipient, let me check my inbox. You can see the spoofed e-mail in . The email seems genuinely sent by an employer of TravelWorld.com.
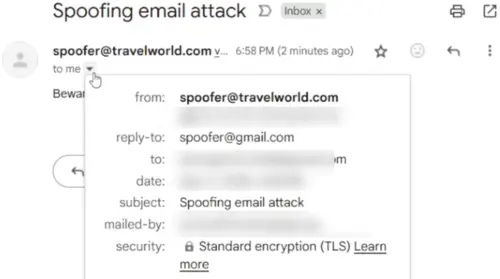
If I expand the email header (), you’ll notice that the reply-to address is different from the impersonated sender’s address.
Why e-mail spoofing is so easy?
You might wonder why it’s so easy to fake someone’s email address. The answer lies in the way email was originally designed. Unlike apps like WhatsApp, Telegram, or Snapchat—where both the sender and receiver are verified on the same platform—email works on a different model. Email is part of a federated system, which means independent servers all over the world exchange messages with each other. There’s no central authority making sure that every sender is who they claim to be. This design keeps email open and widely accessible, but it also leaves gaps for abuse. Think of it like traditional postal mail. If the system doesn’t verify who’s dropping a letter into the mailbox, anyone can write any name in the “from” field. That’s essentially how email spoofing works.
Conclusion
We should never take digital communication at face value. No system is completely secure, and attackers are constantly inventing new tricks to exploit gaps in technology and human behavior. Email spoofing is just one example—it shows how something as common as an inbox can be manipulated to mislead users. That doesn’t mean we should stop using email or other digital platforms. Instead, it means we need to approach them with caution. Always verify the source before clicking links or downloading attachments. Pay attention to subtle signs like mismatched domains, unusual requests, or poorly written content. And whenever possible, use extra layers of protection such as spam filters, and security awareness training.
At the end of the day, security is less about achieving perfect safety and more about reducing risk. By staying alert and questioning what lands in our inbox, we can make it much harder for attackers to succeed.
Author
Anurag Gupta is an M.S. graduate in Electrical and Computer Engineering from Cornell University. He also holds an M.Tech degree in Systems and Control Engineering and a B.Tech degree in Electrical Engineering from the Indian Institute of Technology, Bombay.
Comment
This policy contains information about your privacy. By posting, you are declaring that you understand this policy:
- Your name, rating, website address, town, country, state and comment will be publicly displayed if entered.
- Aside from the data entered into these form fields, other stored data about your comment will include:
- Your IP address (not displayed)
- The time/date of your submission (displayed)
- Your email address will not be shared. It is collected for only two reasons:
- Administrative purposes, should a need to contact you arise.
- To inform you of new comments, should you subscribe to receive notifications.
- A cookie may be set on your computer. This is used to remember your inputs. It will expire by itself.
This policy is subject to change at any time and without notice.
These terms and conditions contain rules about posting comments. By submitting a comment, you are declaring that you agree with these rules:
- Although the administrator will attempt to moderate comments, it is impossible for every comment to have been moderated at any given time.
- You acknowledge that all comments express the views and opinions of the original author and not those of the administrator.
- You agree not to post any material which is knowingly false, obscene, hateful, threatening, harassing or invasive of a person's privacy.
- The administrator has the right to edit, move or remove any comment for any reason and without notice.
Failure to comply with these rules may result in being banned from submitting further comments.
These terms and conditions are subject to change at any time and without notice.
Similar content




Past Comments (1)
test